Is Konnech Conducting CCP Backed Espionage Against the US Military?
Konnech has defense contracts with the US military. Is that data also being leaked to the Chinese government as well?
U.S. election company, Konnech Inc.’s CEO and founder, Eugene Yu, was recently arrested on conspiracy charges and for sending sensitive U.S. election related data to Chinese servers that are physically located in China. The way the Chinese government’s internet law works is such that anything which enters the Chinese internet belongs to the Chinese Communist Party (CCP). Contrary to legacy media reporting, the data stored on the Chinese servers allegedly contained a lot more than 1.8 million poll worker’s personal identifying information. Konnech is known to also store on its servers the location of voting machines, building schematics and many other kinds of sensitive election data that could be useful to CCP state-backed hacker groups.
Needless to say, this is an astonishing breach of national security and it shows that our election systems in the U.S. are far from secure. If this was intentional, one might even define such an action as blatant espionage on behalf of the Chinese Communist Party. Just imagine for a moment what a CCP backed hacking collective could do with such sensitive election related data.
The Chinese government is known to sponsor hacking groups to infiltrate critical infrastructure of the U.S. government, often targeting the military. It is such a big problem that the National Security Agency (NSA) recently put out an advisory of common vulnerabilities exploited by Chinese state-sponsored cyber actors. A few recent occurrences, of Chinese government backed malware infection, were targeting the same kind of SQL servers that Konnech uses to store its data. This kind of malware infection was such that the threat actor is able to “fully control the server machine and use this backdoor to conduct reconnaissance in the internal network.”
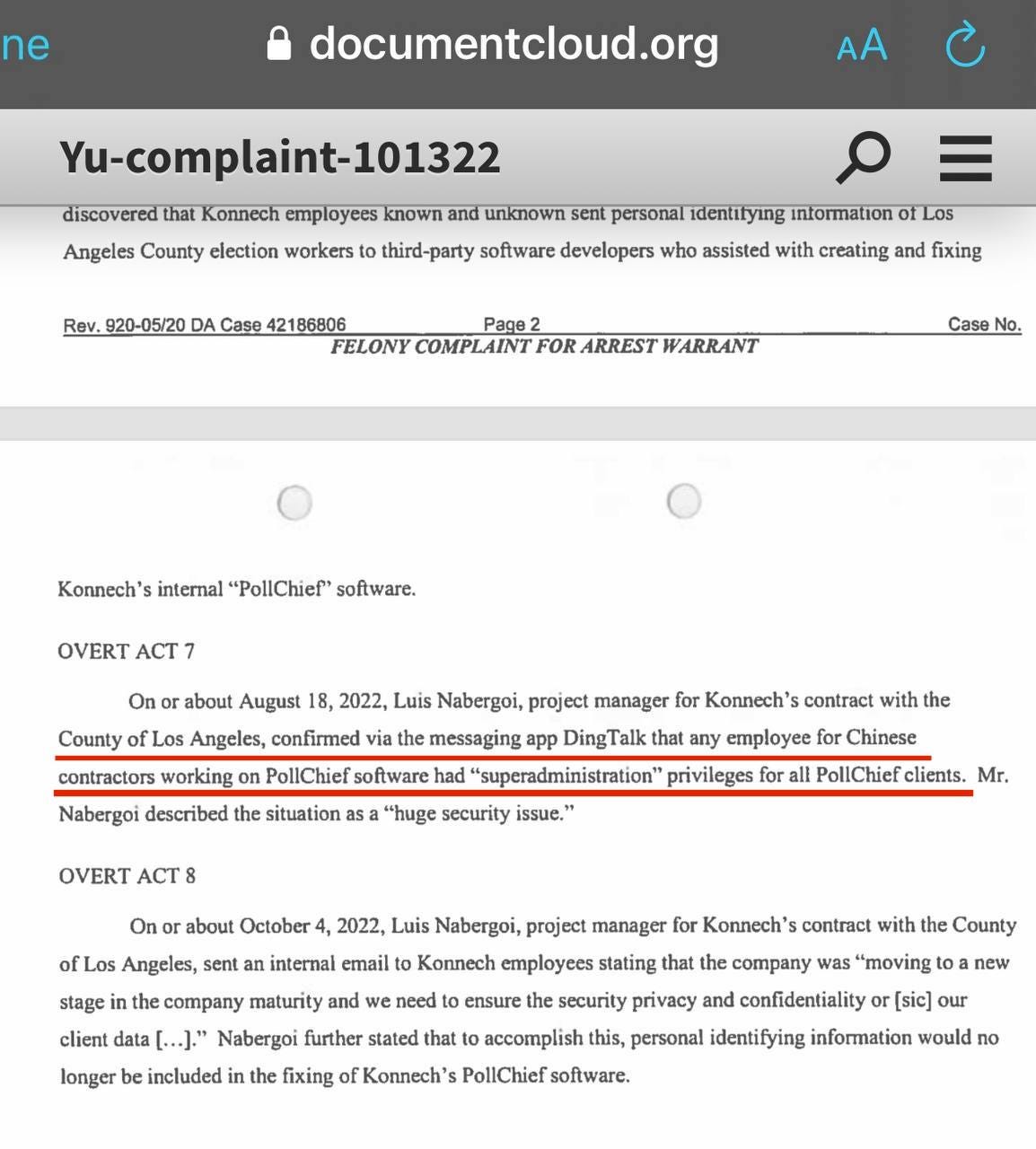
In recent court documents, it was revealed through internal Konnech employee emails, sent by project manager, Luis Puente Nabergoi, (who previously worked at Scytl for over 6 years,) that the Konnech employed Chinese coders, in China, were given “superadministration” access to the company’s systems.
It doesn’t take much imagination to consider the kind of uninhibited field day that CCP state-sponsored hackers could have with our election systems if they had “superadministration” privileges. This is especially disconcerting when considering the prospect of any potential SQL malware allowing hackers to “fully control” the server machines.
At this point, it’s a fair question to ask: does Konnech’s software have malware embedded into it? According to Konnech, they provide their election services to “thousands of election offices across North America.” Do those election offices, which use Konnech’s products, have any CCP backed malware infecting their systems? The Konnech employed Chinese coders already had “superadministration” access to their systems. Are any of these coders part of the Chinese government’s state-sponsored hacking groups?
Eugene Yu and Konnech’s connection to the Chinese Communist Party has now been proven and well documented.
Among the plethora of products that Konnech offers, such as scheduling systems for elementary schools in the U.S. — is an app for overseas absentee voting for the U.S. military, called AbVote. Given Konnech’s recent data leaks, does this mean that any U.S. military service members abroad who download the AbVote app to their phones could potentially be having their personal data syphoned off of their phones and over to the Chinese government?
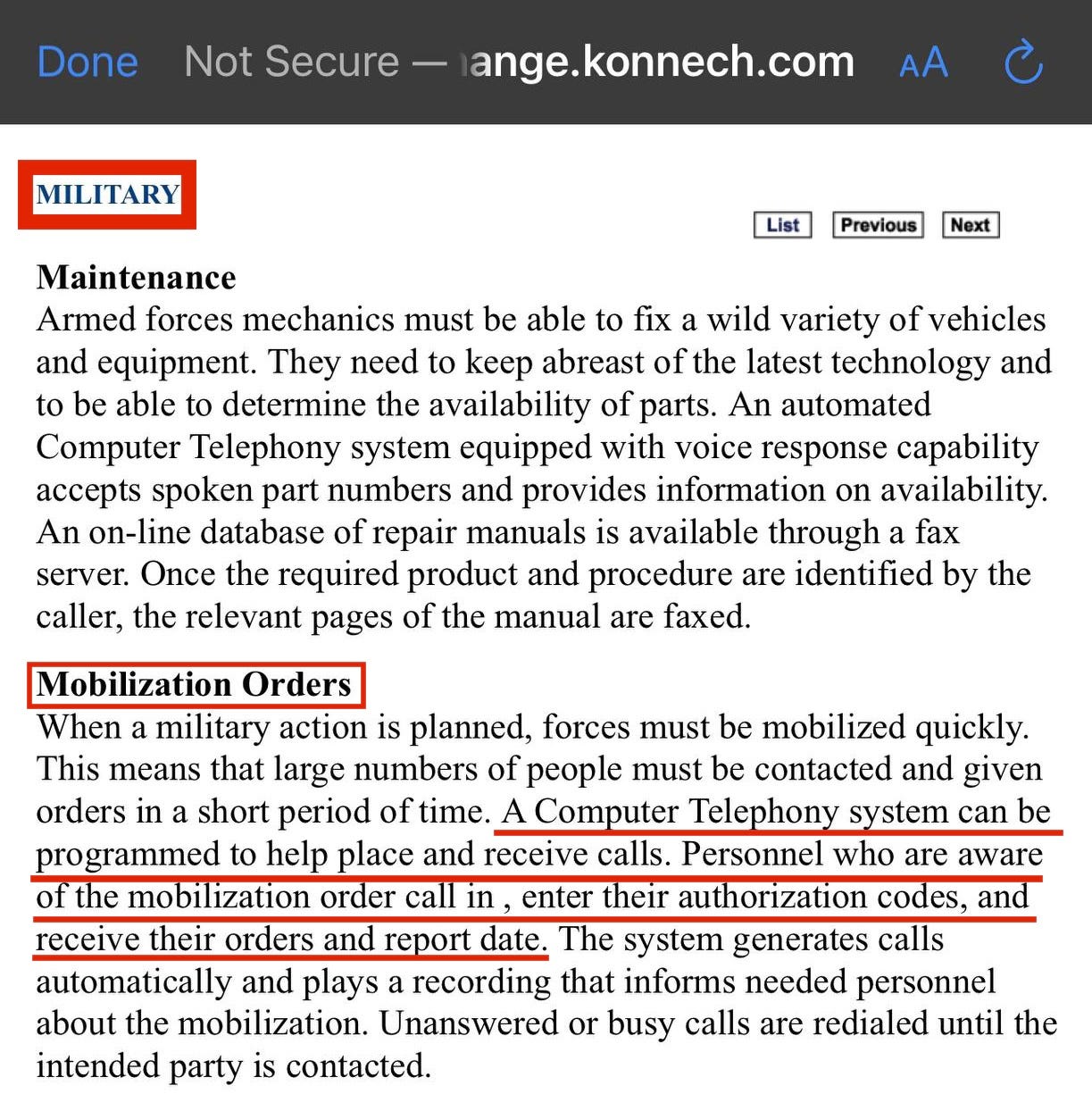
Furthermore, another service offered by Konnech, is the programming of top secret military mobilization orders and missions.
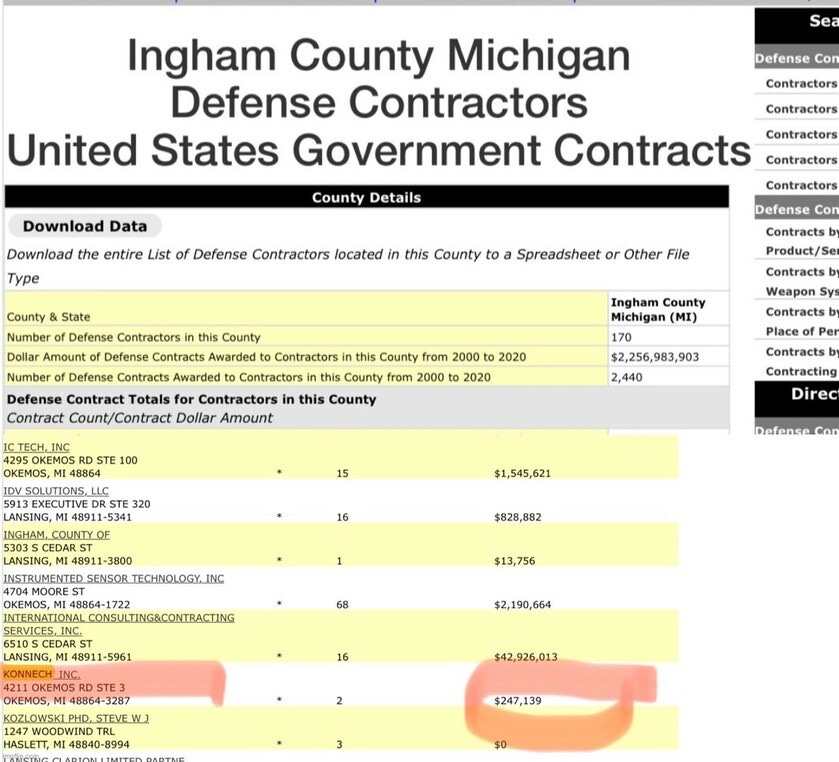
It is extremely disturbing to learn that a CCP connected software company could be providing the U.S. military with their top secret missions and mobilization orders— especially when the CEO of the CCP linked company has been known to leak sensitive data to the Chinese Communist Party. It is unknown whether this military function offered by Konnech is actively in use right now, but Konnech does currently hold defense contracts with the U.S. government in Michigan.
Moreover, the absentee voting product created by Konnech, AbVote, which is used by the U.S. military, was recently acquired by a company called Votem. Eugene Yu currently sits on the board of Votem.
Astonishingly, the Department of Homeland Security (DHS) made Votem a founding partner in the DHS Security Council on Elections.
One might think that the Department of Homeland Security would have a much more rigorous vetting process than to make one of the founding partners of such an important and sensitive role — a company which has a board member that runs elections for the Chinese Communist Party — and leaks election data to the Chinese government.
This council, known as the “Election Infrastructure Subsector Coordinating Council Charter“ (EISCC), aka SCC, is an organization which describes itself as responsible for serving “as the primary liaison between the election subsector and federal, state, and local agencies, including the Department of Homeland Security (DHS), concerning private election subsector security and emergency preparedness issues.”
The EICC is also tasked to facilitate the “sharing of information and intelligence about physical and cyber threats, vulnerabilities, incidents, and potential protective measures.”
Knowing what we know now about Eugene Yu, it really begs the question: why would a company with a CCP linked board member be appointed by the DHS to such a critical role in election security? Could this perhaps be a conflict of interest?
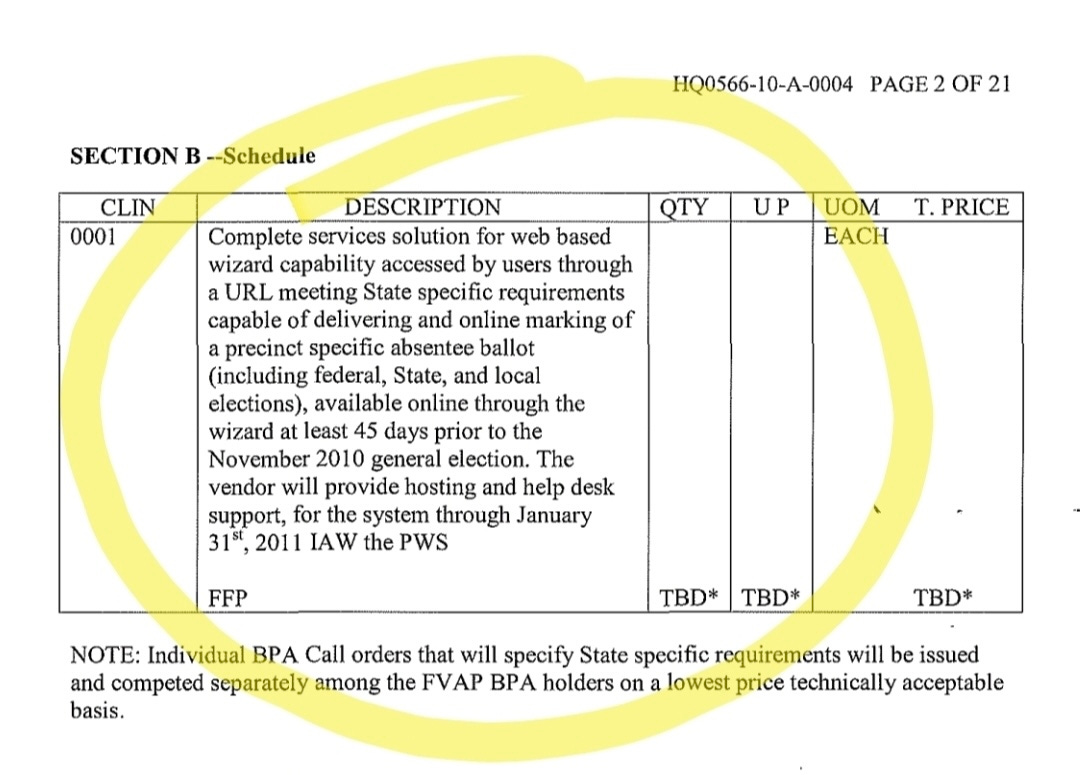
Additionally, in 2010, Konnech secured a 5.4 million dollar contract with the The Department of Defense (DoD).
According to a 2010 article, the DoD initially “declined to release the dollar amounts of the contract awards granted… citing two exceptions to federal acquisition regulations, one of which applies as long as a single contract is not expected to exceed $100,000.” However, documents show that the contract well exceeded that amount to the tune of $5,400,000.
In the 2010 article, it states that “Konnech President Eugene Yu declined to release the figure that company will be paid to deliver blank ballots for Nevada, Montana and New Jersey.” The DoD contract suggests Konnech was contracted to deliver “online marking of a precinct specific absentee ballot (including federal, State, and local elections)”.
We now know that Konnech leaked sensitive election related data to China, allegedly containing the personal identifying information of 1.8 million poll workers, locations of voting machines, building schematics etc. However, this is only one instance that we know of. Could there have been other such instances of similarly astonishing national security breaches? We now know that the Konnech employed coders in China were given “superadministration” access to the company’s election systems, which were used by “thousands of election offices across North America”. What other sensitive data might they have gained access to? Chinese government internet law would have made whatever data they may have accessed into the property of the Chinese Communist Party.
Why would such a company with ties to the CCP, be given defense contracts with the U.S. government? Were Konnech’s coders in China given “superadministration” access to that information as well? If so, wouldn’t that mean that, due to Chinese government’s internet law, the military data accessed by Konnech is now property of the Chinese Communist Party? Does Konnech currently provide their programming services of military mobilization orders for the U.S. Armed Forces? If so, do Chinese coders have “superadministration” access to this information as well? Due to the Chinese government’s internet laws, wouldn’t that top secret information also be in the possession of the Chinese Communist Party?
These are astonishing prospects to consider and the potential national security risks are sobering, to say the least.








Fantastic work. Keep writing!
Nice reveal. Our Military has been attacked in several ways of late. Cyber attacks, Clot shots and Wokeism and it seems the DHS is more focussed on monitoring private citizens. Who is the real enemy? Great job! Thanks.